Right in this Article, I’m Going to Show you Different ways in which Gmail account password can be Hacked!! On Internet , 95% of the Tools we Find on many Websites are Hopeless. It Doesn’t mean that there is no way to hack Gmail, Yes there are few ways that can apt for Hacking.
Gmail Hacking
Gmail is a free Web-based e-mail service currently being tested at Google that provides users with a gigabyte of storage for messages and provides the ability to search for specific messages.
The Gmail program also automatically organizes successively related messages into a conversational thread.
Ways to Hack Gmail Account Password!
I’ll show you 5 ways to hack a Gmail Account:
PASS BREAKER
PASS BREAKER is the only legit tool available on the internet that can really hack a Gmail account. Developed by a hacker, it is used by thousands of users per day who want to hack Gmail passwords. Today, the only quick and efficient solution is PASS BREAKER. This app is unique because it is smartphone, tablet and computer compatible.
Here is how it works:
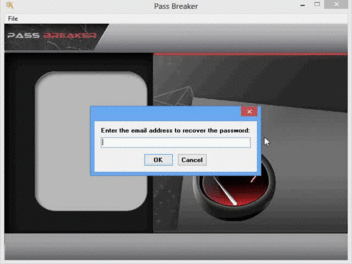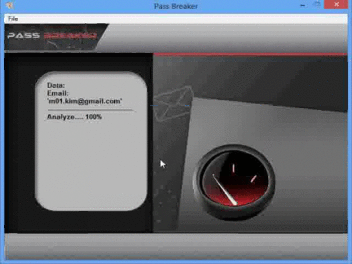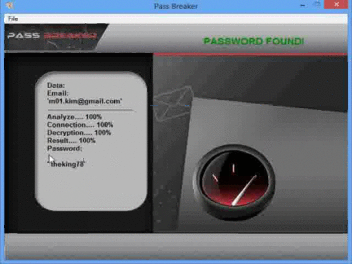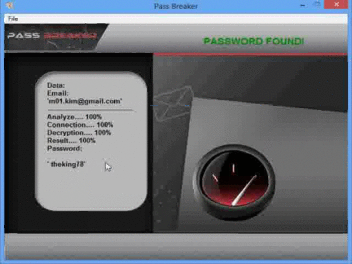
Once you have downloaded it and run it, PASS BREAKER will only require a Gmail email address to hack the password and show it on the screen of your device.
You can download PASS BREAKER here: https://www.passwordrevelator.net/en/passbreaker.php
- NOTE: HackeRoyale does NOT claim or guarantee about the proper working or functioning of this tool. These are purely views of the author & in no way related to HackeRoyale’s own views or interests. Please think twice before taking any step further. HackeRoyale will NOT be responsible in any manner for if the tool doesn’t work as per the expectations. We DO NOT guarantee the authenticity or legitimacy of the tool. Hence, beware!
Phishing
Phishing still remains to be an extremely effective way for hackers to steal login credentials, payment card information, and a multitude of other types of data.
Watch Our Exclusive video on GMAIL Phishing below, to explore more!
Essentially, the hacker tries to setup a website that looks and behaves exactly like another website – which, in this scenario, is Gmail.
![How to Hack A Gmail Account Password In Minutes [All Methods Described] ?! : Tutorial](https://www.hackeroyale.com/wp-content/uploads/2017/06/14-300x169.png)
All the attacker really needs to do is copy the web code from the login screen, add a small amount of PHP code, and then harvest usernames and passwords.
After the false phishing site has been setup, the hacker then sends links of the bogus site to all of their victims.
A careless user won’t see that the URL is slightly different and will consequently send their username and password straight into the hands of the attacker.
Then the phishing site typically redirects the user to the genuine site to avoid suspicion.
Though there are a lot of phishing filters and web URL blacklists that attempt to stamp out phishing, there are always new phishing sites popping up, and there is nothing we can do to eliminate them completely.
Keyloggers
A keylogger is probably one of the most effective and popular ways to hack information.
A keylogger is a type of software that runs in the background of the target’s computer, recording every single keystroke they enter.
Though many advanced hackers employ complex methods of installing keyloggers remotely, such as embedding the program in a P2P file download or other type of software, even novices can install these programs if they have access to the target’s computer.
However, some keylogger programs have tools that help the attacker complete the installation remotely, such as Realtime-Spy.
And hardware keyloggers are even easier to install, because they typically look like a PS2 jack of USB flash drive that can easily be inserted into the back of a desktop computer – without the target being any wiser.
Many of them are even undetectable by the latest anti-virus and anti-spyware software.

![How to Hack A Gmail Account Password In Minutes [All Methods Described] ?! : Tutorial](https://www.hackeroyale.com/wp-content/uploads/2017/06/kusb_inst1m-300x162.gif)
Social Engineering
Social engineering has remained another effective alternative for hackers to steal users’ login credentials.
The idea is to impersonate another individual or to dupe the target into willingly forfeiting their login credentials, and there are several ways to do this.
The first way is to create a false account that has an address that looks like it belongs to a friend, acquaintance, or colleague of the victim.
Then there are a variety of lies a hacker can tell, like they need your login information to recover their account, etc.
In addition, hackers often mimic administrators or Google employees in an effort to garner more trust from their victims.

Some spam emails claim that Google was recently hacked and that they need your username and password to check if your account has been compromised.
But Google employees will never ask you for your account information, so remember that you should never hand over your login credentials to a third party – even if they seem to be legitimate.
Stealing Cookies
There are a number of ways to steal cookies from other users’ sessions and to inject the into your own web browser.
Tools like Firecookie, Wireshark Cookie Injector, GreasMonkey for Firefox, and a myriad of other tools will allow you to sniff out a cookie on the local LAN and then use that cookie to hijack the user’s session.
Also read : How to hack Facebook in a minute !
The easiest place for a hacker to perform this attack is on public Wi-Fi networks like those found at cafes, but some hackers engage in war driving to find weak or exposed wireless networks.
The bottom line is that once the cookie has been stolen, the attacker can then login to the account and read emails, send emails, and change account settings to block the original user.
Things we need to follow to Reduce the chances of being Hacked !
- First and foremost, make sure you never give your password out to another individual even if they’re your friend.
- Always make sure that you log out of Gmail when you are finished perusing your email to avoid becoming the victim of session hijacking.
- Everyone should be regularly scanning their computer with antivirus and antispyware software to help decrease the chance of becoming infected with a keylogger and other similar types of dubious programs that lead to someone hacking your Gmail account.

![Plain White Background Hd Images Pictures - Becuo How to Hack A Gmail Account Password In Minutes [All Methods Described] ?! : Tutorial](https://www.hackeroyale.com/wp-content/uploads/2017/07/Plain-White-Background-Hd-Images-Pictures-Becuo.jpg)
No comments:
Post a Comment